Page History
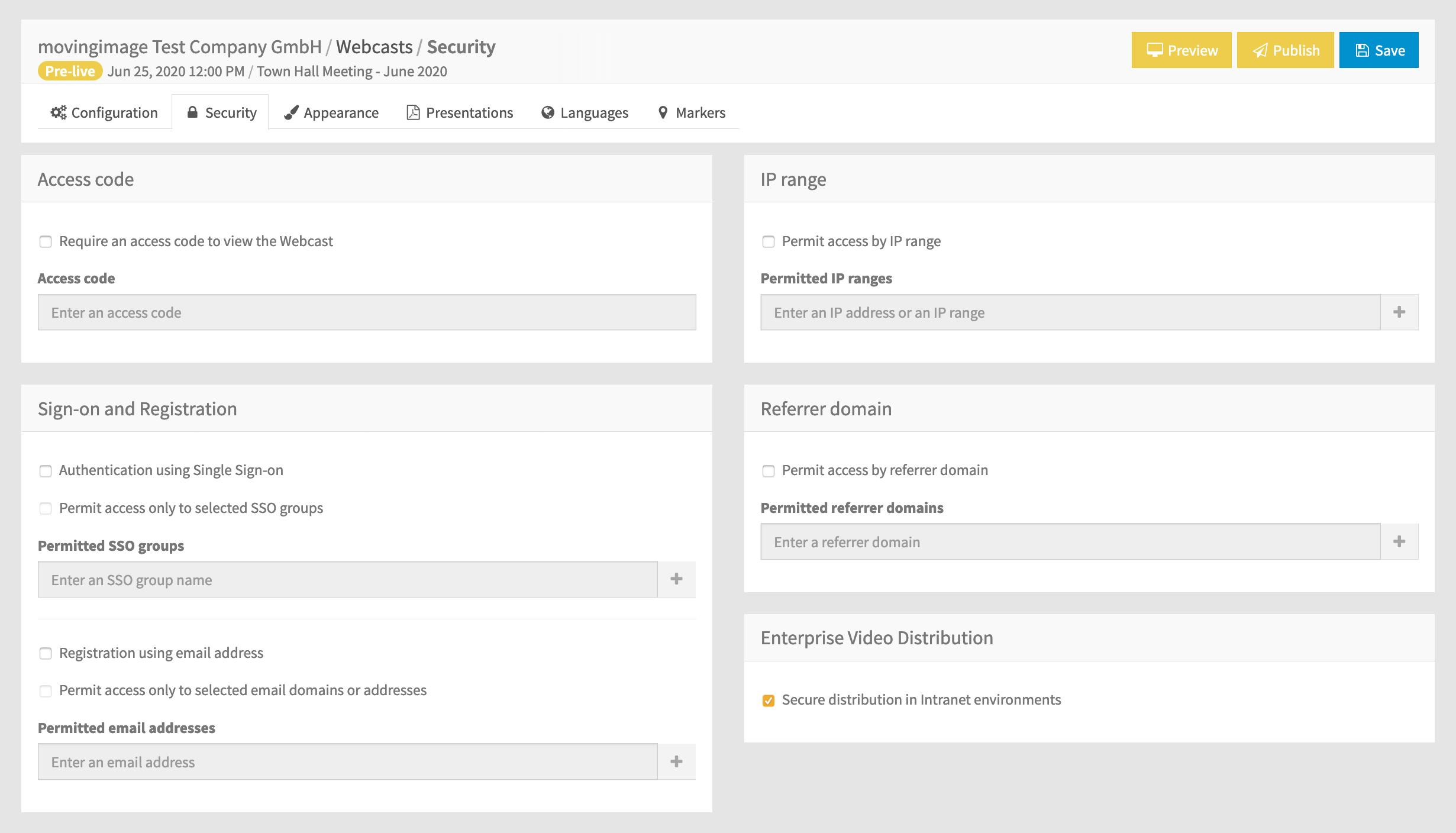
In the "Security" tab, you can set up permissions for accessing decide who can access a Webcast in the WebcastConsumer.
You can allow access:
- only to browsers connecting with certain external IP addresses
- only to browsers referred by link to the Webcast from certain domains
- only to viewers registering with specific email addresses or domains
- only to viewers who enter a pre-defined access code
- using a HMAC token.
You can configure combinations of these options, in which case all sets of conditions must be satisfied before access is granted; : the IP range is checked first, then the referrer domain, then the password and finally the registered email address.
If configured for your account, you can also enable or disable Peer-to-Peer video distribution. When enabled, the live video traffic is distributed within your network, reducing pressure on your company's external network bandwidth.
SSO Groups
Wildcard group names (indicated by the * symbol) are now supported for SSO groups.
...
- Hive (using a Java client)
- Hive (using WebRTC)
- Kollective
HMAC token authorization
| Info |
|---|
The HMAC token is generated client-side and follows a specific standard. Please contact your administrator for more information about implementation used by your organization. |
This security feature ensures that only authorized users are able to access a protected Webcast.
Specifically, this feature verifies if the HMAC token provided by the viewer is valid.
Speak to your Account Manager for further details.